MAX Intelligence: Crimes Targeting Crypto Holders Escalate Globally
- MAX Security
Table of Contents

Global assaults and kidnappings of crypto holders escalate, as criminals exploit security gaps and rising digital asset values to target digital wealth.
Executive Summary
-
There is a growing trend of physical risks targeting cryptocurrency holders in multiple countries in 2025, which coincides with the increasing adoption and market value of digital currencies.
-
Threat actors, from cybercriminals to local criminal networks, are increasingly leveraging physical coercion to maximize financial gains through cryptocurrency. Main tactics include staged encounters and kidnappings, home invasions, often facilitated by OSINT methods.
-
The combination of cryptocurrency’s anonymity, liquidity, and high Return on Investment (ROI) continues to incentivize perpetrators. This risk is amplified by low entry barriers for non-professional actors accessing wallet-linked intelligence and behavioral data.
-
Enhance physical security protocols and increase threat awareness for individuals associated with the cryptocurrency industry and infrastructure, particularly those with significant holdings and high public exposure.
Overview
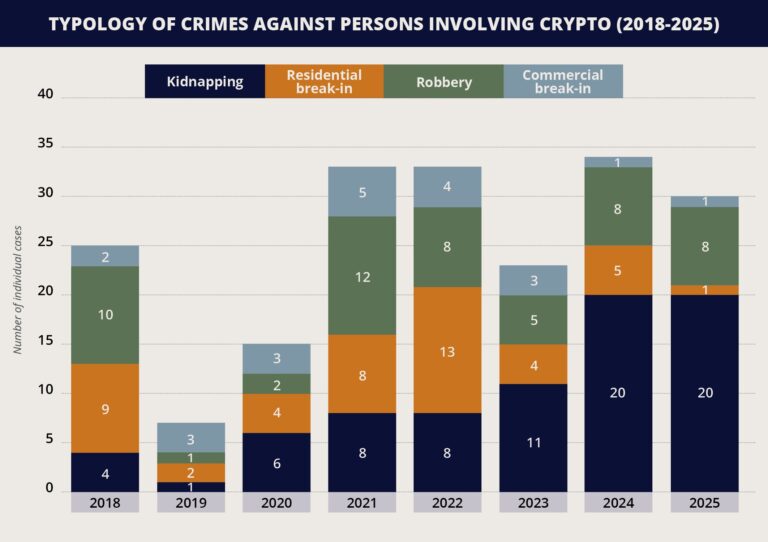
Across the globe, in several countries, primarily France and USA, there have been incidents involving the targeting of people within the cryptocurrency industry by perpetrators for forceful ransom in recent months. These are not opportunistic crimes in which crypto happens to be the payment method. Rather, perpetrators are deliberately selecting victims based on their confirmed or perceived possession of digital assets. This trend is exemplified by the increase in reported kidnap-for-crypto incidents from eight globally in 2022 to 20 in 2024, and at least 20 already recorded by June 20 in 2025. This excludes other forms of violent crime involving the transfer of cryptocurrency. In this emerging pattern, victims are abducted or coerced into transferring cryptocurrency in a targeted manner, typically under physical threat or psychological pressure.
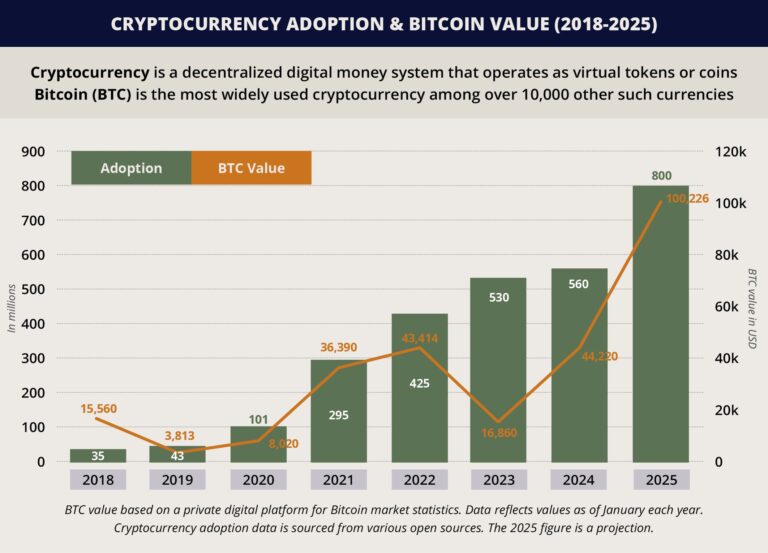
Cryptocurrency is especially attractive to perpetrators due to its anonymity, liquidity, and the fact that transactions are largely irreversible, unlike bank transfers, which can often be frozen or traced. Moreover, public visibility on social media, blockchain transparency, and high media exposure make crypto holders perceived to be wealthy, easy to identify, and monitor, especially when they publicize wealth or participate in crypto events. C-suite executives with significant crypto holdings may be increasingly targeted because of the absence of protection measures, particularly in start-up or consultancy environments that lack formal physical security protocols. Unlike senior figures in legacy financial institutions, founders of cryptocurrency firms may operate without access control, personal protection, or adequate risk management procedures, which increases their security vulnerability. Furthermore, individual investors or mid-level professionals working in the crypto sector, like wallet engineers, infrastructure developers, and crypto custody personnel, like over-the-counter (OTC) traders and brokers, have also become targets of physical threats. Moreover, the growing value and consequent ownership of cryptocurrencies, from 18 million in 2018 to over 560 million in 2024, partly increases the number of individuals who face the risk of being targeted.
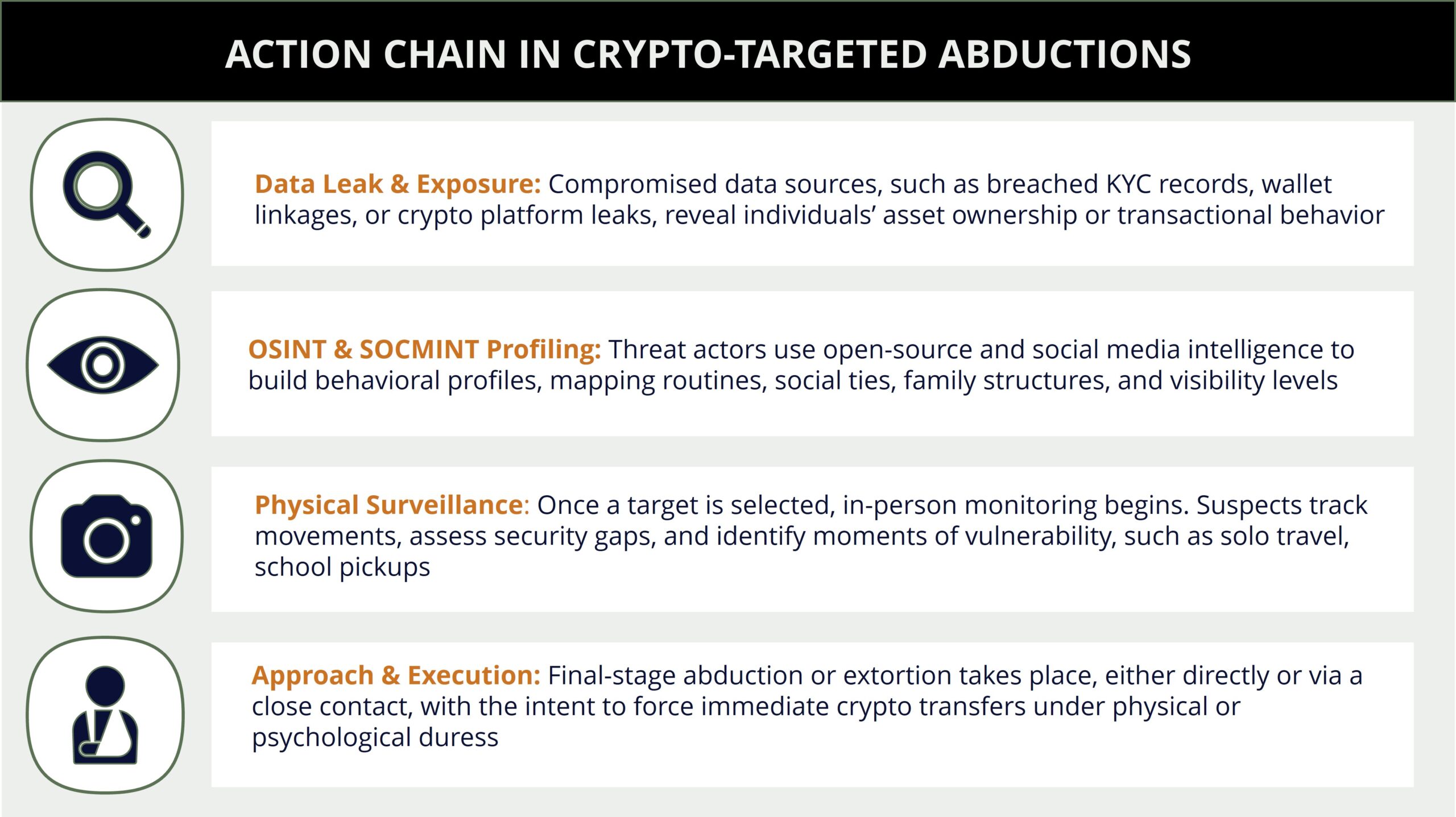
Criminals adopt standard abduction tactics enabled by online exposure, behavioral profiling
Several recent incidents reveal a consistent operational pattern among criminals seeking to extort cryptocurrency through physical coercion targeting those involved in the crypto industry. While specific tactics may vary by context, the overarching logic is similar. Identify a high-value target, isolate them or someone close to them, and subject them to psychological or physical threats until access to digital assets is obtained. The most common tactics involve the combination of the following strategies.
The first stage typically involves surveillance and social profiling. While not exclusively, often times rather than relying on sophisticated cyber intrusions and hacking, criminals start with passive reconnaissance, leveraging what the target has already made public. For instance, social media platforms, as well as blockchain explorers and footage from crypto-related events, provide exploitable information. Criminals may rely on an individual’s online presence or visibility at crypto conferences and events, where financial success is either implied or openly showcased, to select and pursue victims without significant security via social engineering techniques. Open-Source Intelligence (OSINT) tools and dark web brokers are used to gather additional information, including map daily routines, identify vulnerable family members, and pinpoint low-security timeframes such as solo travel or personal out-of-home activities. In several cases, criminals reconstructed entire behavioral patterns based on digital footprints alone, underscoring how visible success in crypto can quickly become a liability.
Once a target has been profiled, criminals may move to stage social encounters. These ambushes are initiated through fake meeting requests, investment pitches, or casual invitations sent via different communication channels, including social media, phone calls, prior in-person meetings, or dating applications. The trap is set under the guise of networking, a practice deeply normalized in the crypto environment. For example, on February 9, a British crypto broker was invited to a meeting with potential clients, who were also British nationals, in an apartment that the “clients” were renting via an online marketplace for short-and long-term homestays in Estepona, Spain. He was threatened upon arrival to transfer 30,000 EUR. Similarly, in January, on Jeju Islands, South Korea, which is touted by authorities to be a crypto-friendly destination, six Chinese suspects arranged a meeting at a luxury hotel with a Chinese OTC trader to swap 690,000 USD in cash for various cryptocurrencies. As the deal progressed, the suspects accused the victim of not providing the agreed-upon crypto and assaulted him. Dating applications, or broadly, romance scams, are also long-term techniques used in multiple countries to lure crypto holders into isolated, in-person meetings or investing in fake schemes to steal cryptocurrencies.
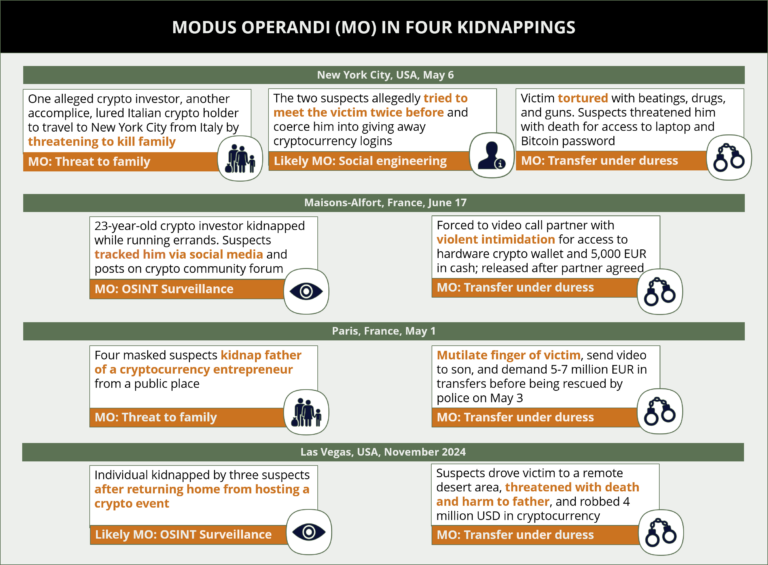
Alternatively, in some instances, perpetrators adopt a more direct approach, avoiding social engineering and engaging in residential or commercial break-ins. Such methods are premeditated and often take place at night or during long weekends, when vigilance tends to be lower. The homes of crypto executives, developers, or investors are likely to be monitored in advance. This tactic was employed in the case of a co-founder of a French crypto security startup, in France, when he and his wife were abducted from their home in Vierzon commune by ten assailants on January 21. During captivity, the kidnappers severed his finger and partly received the ransom in cryptocurrency, with authorities rescuing the two victims after 48 hours. In other cases, cryptocurrency exchange centers, typically Bitcoin ATMs, are targeted in both premeditated as well as opportunistic commercial break-ins. The frequency of such break-ins is higher in countries with higher installations of Bitcoin ATMs, like the USA, Canada, Australia, Spain, and Georgia, among others. Suspects may resort to directly stealing the currency exchange machines or their components, such as cash boxes, coerce on-site workers to grant access to force currency transfer, or themself install malicious software into the ATM and re-route transactions.
In some cases, instead of targeting the crypto holder directly, perpetrators may exploit a more psychologically potent vector by kidnapping family members. This approach leverages emotional pressure and can often result in faster compliance from the victim in making the crypto ransom transfer. In Paris, France, on May 13, at least four assailants unsuccessfully attempted to abduct the daughter, son-in-law, and grandson of the CEO of a Paris-based crypto exchange platform during the daytime on a public street. The cases exposed a recurring blind spot in executive security planning, from the assumption that the threat stops with the principal, while family members remain unprotected. Once a sense of control over the victims is established, either through physical intimidation or psychological domination, they are expected to move to execute a live transfer under duress. Victims are coerced into unlocking wallets, revealing seed phrases, or initiating transactions in real time while facing heightened threats.
Assessments & Forecast
Physical risks against individuals involved in crypto industry are expected to increase in high-crypto adopting countries, emerging markets
The modus operandi used by perpetrators in recent incidents involving physical threats against individuals associated with the crypto industry has highlighted a systematic approach to victim selection. Several of these incidents showcased the criminals targeting individuals who had both substantial crypto assets and exhibited visible, exploitable vulnerabilities. These incidents also demonstrated how illicit actors are now approaching digital wealth acquisition. While cyberattacks, such as phishing, malware, or exchange breaches, remain a dominant method for stealing crypto assets, a subset of perpetrators are resorting to physical coercion as an alternative or complementary tactic. For example, in the USA, a Florida-based 13-member gang evolved from SIM swaps and other cyberattacks into 11 separate coordinated home invasions of crypto holders to physically coerce and forcefully attain crypto assets between 2022-2023. This evolution does not necessarily reflect a change in the type of actors involved, but rather a tactical diversification by criminal networks that previously operated exclusively in cyberspace or other types of physical, albeit non-crypto related, crimes.
The hindrances to being able to perpetrate physical attacks targeting individuals associated with the crypto industry are decreasing. While organized criminal groups remain involved, a broader array of actors with varying sophistication levels, including well-experienced and semi-professionals, are entering the space. To some extent, this is driven by the widespread availability of personal information of individuals either available through OSINT or through Initial Access Brokers (IABs) on the dark web, who sell access to compromised individuals and networks in the cybercrime ecosystem across various sectors, including cryptocurrency, often through phishing and different malware techniques. As such, leaked KYC records of individuals associated with the crypto industry would also potentially aid in victim selection for targeted physical threats. This is buttressed by the event of a data breach of a well-known US-based cryptocurrency exchange firm on May 11, when attackers exploited a third-party vendor to access confidential user identification data, including names, physical addresses, phone numbers, and submitted ID documents. While the company confirmed that funds remained secure, the incident exposed tens of thousands of KYC-linked records. Although there is no indication of any direct link between such KYC breaches and associated violent crime targeting individuals associated with the crypto industry, the incident demonstrates how leaked personal data can potentially become available to criminal elements, thus heightening the overall risk. The widespread availability of such information is also demonstrated by the increase in the reported ransomware victim listings by IABs on dark web forums from 2,598 in the first half of 2023 to 4,318 in the first half of 2024.
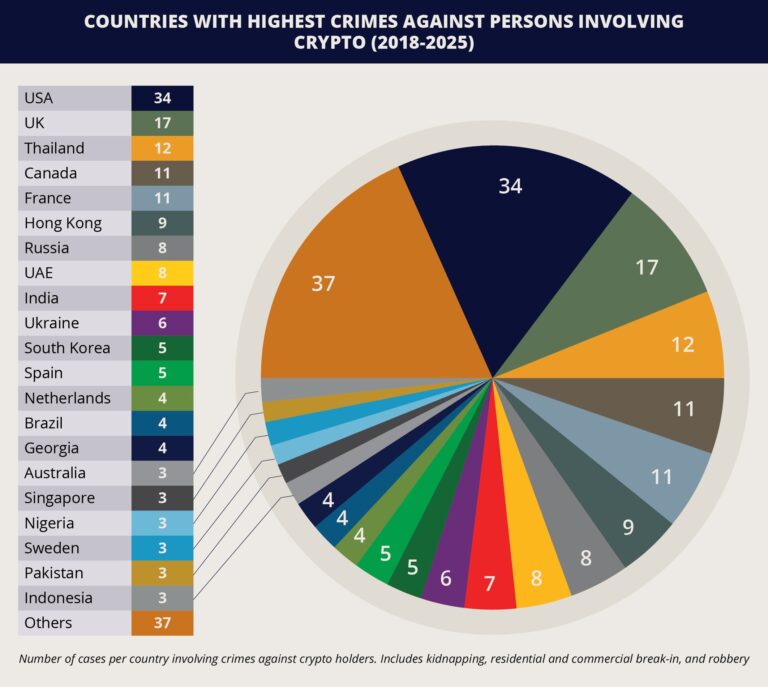
While some actors behind attacks against individuals associated with the crypto industry are closely associated with cybercriminals, such as in the Florida-based gang case, others are organized crime affiliates with little technical expertise. In these cases, threat actors rely on externally sourced data and deploy low-tech, high-impact methods like home invasions or staged encounters. For example, in Thailand, perpetrators associated with Russian criminal networks were involved in at least 10 reported violent crimes against crypto investors, mostly from Russia. Loosely structured criminal networks from Russia or eastern Europe have maintained a long-standing, yet largely low-profile presence in Thailand over the years, with phishing scams, sex trafficking, and money laundering being traditional activities in major tourist hubs. The recent cases, however, indicate increasing diversification of their criminal activity to include the targeting of crypto holders, potentially aided by an already established presence in Thailand. More recently, in Bali, Indonesia, a Russian national suspected to be a gang leader was arrested for a kidnap-for-crypto case in December 2024. The suspect, along with eight other perpetrators, ambushed and abducted a Bali-based Ukrainian crypto trader in the remote coastal resort town area of Ungasan, and forced to transfer crypto assets worth 196,000 USD. This variation of the profiles of the perpetrators and the potentially wider geographical reach of criminal networks makes threat anticipation more complex and elevates the overall risk for individuals associated with the crypto industry.
FORECAST: Going forward, high-ranking executives and founders of crypto platforms will remain the top targets. Wealth is the primary motivator for such crimes, but among these high-profile individuals, those with specifically a lot of public visibility have higher chances of being targeted by criminals because of the easily available personal information. Executives often have a strong online presence, which makes it easier for criminals to identify, monitor, and eventually approach them. Coupled with the use of potentially leaked KYC data and blockchain address tracing, this facilitates the process for threat actors to locate individuals with significant crypto holdings. Meanwhile, family members of high-net-worth individuals associated with the crypto industry will continue to be used as leverage, as seen in the two cases in France, especially in environments where the primary target maintains strong personal security while the family members usually do not.
Similarly, high-net crypto holders who are not primarily and professionally involved in the sector can potentially be at increased risk of targeted armed robberies, including as part of home invasions. To a lesser extent, crypto wallet engineers, infrastructure developers, and crypto custody personnel, like OTC traders, would also face increased targeting as their critical role becomes known by members of organized crime. For example, in December 2024, a software engineer working in the crypto sector was lured through a social media platform and summoned to a meeting at a high-end hotel in Chengdu, China, where he was coerced into transferring the equivalent of six Bitcoins (BTC) to the perpetrators’ digital wallet. This incident demonstrates that, rather than exclusively targeting high-profile individuals, perpetrators may increasingly focus on low-profile, high-value individuals with proven crypto holdings and association with the sector.
FORECAST: Cyberattacks will likely remain the preferred mode of theft of digital assets and sensitive credentials for large-scale or anonymous operations, particularly where technical means offer low risk of exposure. These include SIM swaps, wallet drainers, exchange exploits, and smart contract manipulation via social engineering. Their appeal lies in scalability, deniability, and automation. However, as cybersecurity defenses become more sophisticated and expensive to bypass, criminals are expected to face higher barriers to success. Penetrating well-secured multi-signature wallets or cold storage systems often requires more than technical skill, as it typically depends on insider access or brute coercion, both of which explain why physical threats are expected to continue regaining utility. These evolving tactics align with the broader shift in crypto-related threat patterns, moving from purely digital exploitation to highly personal, kinetic forms of violence that target irreversibility and speed of cryptocurrency transactions. That being said, this convergence underscores the need for layered countermeasures, including multi-signature protocols, time-locked smart contracts, duress-triggered transactions, and architectural separation of access credentials, to limit potential losses or delay unauthorized access in the event of physical threats. However, any real-time resistance against forced payments may carry a significant risk of violence.
FORECAST: Despite the utilities of physical attacks, they carry a higher likelihood of detection and arrest, especially in jurisdictions with strong law enforcement capabilities. Regardless, the number of actors willing to engage in physical extortion is expected to grow moderately, driven by rising crypto values and growing adoption of digital assets, with returns often exceeding those from traditional robberies or kidnapping-for-ransom tactics, despite similar risks of detention. On this note, Bitcoin values are expected to remain relatively elevated, with reported forecasts projecting prices averaging in the range of 130,000 and 200,000 USD during 2025. Thus, the current trend of increasing physical threats against crypto investors is expected to persist at least in the coming months through 2025.
FORECAST: Physical crimes will likely be more prevalent in regions where growing crypto adoption converges with the presence and capabilities of local or even more organized criminal networks, notably in western Europe, Canada, USA, South Korea, Russia, Ukraine, Hong Kong, and emerging hubs like Argentina, Brazil, India, Pakistan, and Philippines. The sharp rise in kidnapping-for-cryptocurrency cases in France, recording 10 out of 20 incidents as of June 20 in 2025, can be attributed to its proactive regulatory stance to position the country as a global hub for crypto innovation, which also manifests as frequent high-profile conferences. While these developments have fostered industry growth, they have also introduced new security vulnerabilities, particularly in urban centers with active organized crime networks. From a regulatory perspective, France’s mandatory public registration of digital asset service providers, in effect since 2019, may inadvertently increase exposure. Stakeholders with insufficient physical or cybersecurity protocols are likely to become targets, as criminals may exploit publicly accessible records to identify and track potential victims. Other countries with high crypto adoption and similar regulatory frameworks, like South Korea or in the European Union (EU), where a law requiring crypto firms to comply with specific transparency and disclosure requirements came into effect in December 2024, may witness relatively high exposure to physical risks.
FORECAST: Moreover, vacation hotspots favored by high-net-worth individuals (HNIs) or moderately net-worth individuals (MNIs) may present elevated physical security risks for crypto-related crimes. Such hotspots may continue to be relatively more commercial and international holiday destinations like Thailand or other regions globally, where criminal networks already operate well-established tourist scams. These may include romance scams targeting unsuspecting foreign visitors, making hotspots for solo male travelers, and sex tourism in countries like Colombia, Thailand, and the Philippines vulnerable to crypto thefts. These may be staged through social engineering techniques via dating applications or in an opportunistic manner after in-person meetings at bars or nightclubs. That said, there will continue to be unpredictability in assessing the potential target locations. This is because a potential victim could be lured to any remote tourist destination under the pretext of a formal or casual meeting, as well as have their travel itinerary tracked via social media surveillance. In comparison, in countries with high crypto adoption but lesser influence of criminal networks, such as Israel and Singapore, the physical risk to crypto holders is likely to be lower. In summary, while cyberattacks are not being replaced, the expanding convergence with physical coercion introduces a broader threat surface and a higher operational cost for crypto exposure.
FORECAST: The wider availability of target data through dark web vendors and OSINT tools will enable mid- and low-tier criminal groups to carry out attacks that previously required sophisticated planning. Replication of tactics is also likely, as threat actors may increasingly influence copycat methods across regions with weak physical protection norms and a wide community of crypto holders. This is plausible given the high financial gains in recent kidnappings and break-ins, with the relative ease of transferring large sums of cryptocurrencies with anonymity compared to traditional methods like theft of hard cash or bank transfer. The latter may involve more logistical challenges like potential processing delays, transaction limits, regulatory red flags, and a higher risk of traceability.
Conclusion
In recent years, the expansion of the crypto ecosystem has been accompanied by a sharp rise in physical threats targeting individuals with digital asset exposure. Threat actors increasingly exploit the anonymity, liquidity, and irreversibility of cryptocurrency to enable high-yield, low-recovery extortion schemes.
This shift has elevated the threat landscape beyond digital vulnerabilities, exposing executives, developers, traders, and even family members to coercive violence. Looking ahead, as crypto adoption deepens globally, threat actors are likely to further refine and replicate these hybrid tactics, especially in countries or situations with limited physical protection standards.
Recommendations
-
Those operating within the cryptocurrency sector are advised to enhance physical security protocols for crypto executives and infrastructure personnel, particularly those with high public exposure or predictable routines. This includes home surveillance, travel security planning, and protective services for close relatives.
-
Consider implementing layered access systems for digital assets, including multi-signature wallets, time-delay mechanisms, and duress-triggered transactions to mitigate the risk of forced transfers under physical threat.
-
However, it is advised to avoid resistance against forced transfers in the event of an abduction or attempted robbery, given the heightened risk of violence.
-
Avoid posting geotagged photos, videos, flaunting luxury items, or sharing travel plans on social media.
-
Routinely alter travel routes and refrain from divulging sensitive itinerary information to strangers. If in need of directions, ask a local hotel concierge, rather than approaching a stranger on the street.
-
Update your office or company of your travel plans and whereabouts. Use travel-tracking or satellite monitoring applications to indicate your location. In the event of an abduction, use the panic button on such apps.
-
Use vetted transportation from a hotel, company, or organization. Avoid meeting strangers or new acquaintances in secluded places.
-
Carry out online exposure assessments of key personnel and remove or obfuscate references linking identities to crypto holdings, wallet activity, or attendance at blockchain-related events.
-
Monitor forums, sites, and channels across the clear, deep, and dark web for exposed data, including leaked KYC records, wallet-linkage repositories, and social media scraping tools, to anticipate and mitigate threat actor reconnaissance.
-
Engage with insurers offering crypto-specific Kidnap & Ransom (K&R) coverage and assess coverage gaps for decentralized or start-up structures where formal protection protocols are often lacking.
For ongoing updates and in-depth reports, explore the MAX Intelligence Portal by signing up for a free demo here. Or learn more about Scout, our new Intel AI assistant trained on over a decade of vetted intelligence reports here.
Cryptocurrency Glossary
Blockchain: Digital database containing records of transactions that can be used and shared within a decentralized, publicly accessible network
Wallets: Hardware device or software program that stores cryptocurrency keys, which allows access to crypto coins
Seed Phrases: Sequence of words that acts as a key to access and recover cryptocurrency funds stored in a wallet
Cold Storage Systems: Device or software for storing cryptocurrency private keys offline
Smart Contract: Self-executing program that automates the actions required in a blockchain transaction
SIM Swaps: A fraud wherein suspects trick a mobile network provider into transferring a victim’s phone number to a SIM card they control
Wallet Drainer: Malicious software used to siphon off crypto wallets
Exchange exploits: Malware tactics, like phishing, which hackers use to steal money or data from cryptocurrency exchange platforms
SCOUT
INTEL AI BY MAX SECURITY
Fill in your details to schedule a demo with our team.